Consumer Protection in the Decentralized Network:
a Mapping of the Research and Policy Terrain*
Chapter for book on Private Networks and Pubic Objectives, edited by Eli Noam, Columbia Institute for Tele-Information, New York, NY
by Rohan Samarajiva
Associate Professor of Communication
The Ohio State University
3016 Derby Hall
154 North Oval Mall
Columbus, OH 43210
V: (614) 292-3713; F: (614) 292-2055; rohan+@eso.edu
Revised December 1993
* The contributions of Peter Shields and Roopali Mukherjee of the Ohio State University to this paper are very gratefully acknowledged. The views expressed in this paper and any errors of fact are entirely the responsibility of the a uthor.
1.0 Introduction
The problem addressed in this chapter begins from the phenomenon of "use privatization," described by Eli Noam (Noam, 1991), more particularly from his concern that operators of private networks will exercise power over persons connecting to the public network through them (1991, pp. 15-16). Noam defines private networks rather broadly--"they are private in the sense of being separate from the public or general network, and they are not open to all in the way that the public network is" (1991, p. 2). T his definition is not hardware or ownership based. It is based on access. Indeed, it suggests that access to the private network is dependent on membership in some social group or organization. When thought of in this way, the phenomenon loses some of its novelty. Organizations such as offices and hospitals used as illustrations have had "membership" criteria and also telecommunication systems governed by internal organizational rules for quite some time. At the simplest level, the household (the unit usu ally considered the "consumer" within the residential segment of the public wireline network) is an organization with its own rules about access to the telephone instrument and thereby to the network it connects to. A pay phone with its technologically em bedded rules governing network access also affects user behavior. So, the phenomenon is actually more general, and more important, than Noam suggests. But the phenomenon has undergone dramatic changes since the liberalization of customer interconnection t o the public network in Carterfone (13 FCC 2d 420 (1968), recon. denied, 14 FCC 2d 571 (1968)) and the proliferation of private networks is deserving of scholarly attention.

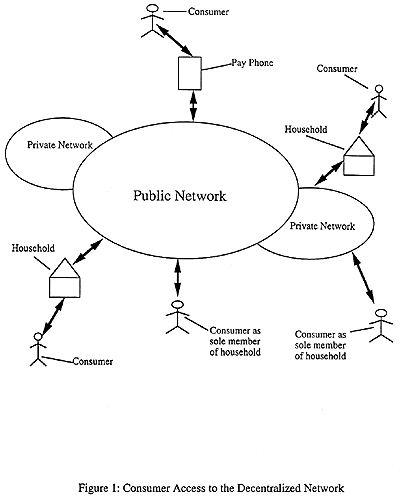
The principal modes of consumer access to the decentralized network are depicted in Figure 1. Of the four principal modes of consumer access to the public network, only one allows direct access--as sole occupant of a household, where the intervening la yer of household social organization is absent. In all other situations, the consumer must go through some form of an intervening layer. In a household, it is the family or other social relationship. In the case of access via pay phone, the pay phone prov ider can constrain and enable the consumer's form of access. Where the consumer is connected to the public network through a private network, the provider of the private network can constrain and enable consumer access. This is in addition to the househol d layer, if applicable.
The above discussion conceptualized the consumer as a "calling party." But almost every consumer is also a "called party." Access to the network is sought not only for the initiation of outgoing calls (faxes, computer messages, etc.);" 1 the ability to receive incoming calls is equally important. Control of the interfaces between various networks, and the design of networks and abutting physical environments can constrain and enable the initiation and the receipt of calls. A private network can be programmed to reject all calls from one or more prefixes or numbers. In jurisdictions where the call reject service of the "call management services" package has been offered, a residential telephone system ( many North American homes have more than one telephone) can be programmed to reject calls from specified numbers without the phone even ringing. Pay phones are frequently programmed to accept no incoming calls at all.
In this chapter, a taxonomy of forms of consumer access to the decentralized network is first developed. Second, a theoretical framework for analysis of policy implications of private control of such access is outlined. Finally, consumer protection imp lications in terms of research and policy are discussed.
2.0 A Taxonomy of Forms of Network Access
At the simplest level, entities participating in the network may be classified as individuals and organizations. Organizations do not actually make calls, individuals call on their behalf, even in this age of automatic dialing and announcement devices and computer-to-computer communication (it is possible to identify an individual responsible for these communications). Thus the classification actually refers to individuals qua individuals and individuals qua organizations. Given the chapt er's focus on consumers, the taxonomy will exclude individuals qua organizations. Individual participants in the network are described as consumers, whether or not they have contractual relationships with network providers. That is, a homeless pers on using a pay phone would be included in the category of consumer.
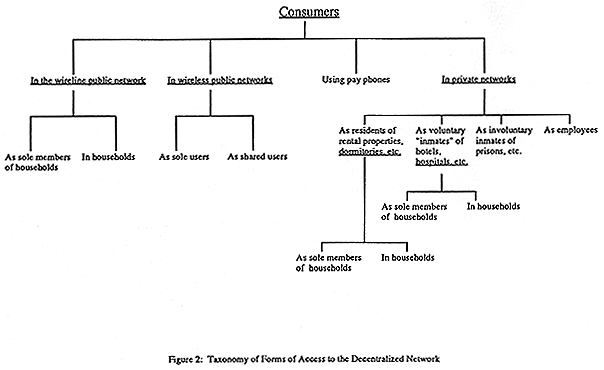
Figure 2 shows the primary modes by which consumers are linked to the network. Consumers can be connected through the ubiquitous, predominantly wireline, public network. They can also be connected through currently non-ubiquitous, predominantly wireles s, public networks, exemplified by cellular networks. The basic distinction between the wireline public network and the wireless public network is that the former was set up as a network connecting immobile physical locations (e.g., rooms in buildings) an d that the latter was set up as a network connecting mobile physical locations (e.g., cars). If the inchoate moves toward personal telephone numbers on the part of wireline network providers and those toward truly portable cellular telephones and personal communication devices on the part of wireless network providers succeed, this distinction may begin to blur. Even if the two types of networks were to converge in terms of functionalities and ubiquity, their different institutional histories would still justify separate treatment.
Consumers may directly connect to the wireline or wireless public networks as sole users, or they may connect as household units. In the former case, there is no intervening social organization between the consumer and the network. In the latter case, the rules of the household enable and constrain the consumer's access to the network. An individual consumer's interests regarding network access may come into conflict with those of other individuals in the household or with the household's rules. It has been customary to conflate household and consumer (perhaps because scholars and policy-makers writing on the subject did not occupy subordinate positions within households), but two recent policy controversies have highlighted the need to open the "black box" of the household.
The first controversy was regarding parental liability for portions of the telephone bill reflecting audiotex usage by minors (Samarajiva & Mukherjee, 1991). Here, the affected parents claimed they were not liable for the high audiotex charges beca use they did not make the calls and/or the network provider's services had been changed in ways that made parental regulation of network access by household members difficult or impossible. These claims were taken seriously by regulators, legislators, and even by the Local Exchange Companies (LECs). Disconnection of complainants from the network, at least with respect to local exchange voice telephony, was generally prohibited and various methods of blocking access to audiotex services were devised and of fered to parents. In many cases, the LECs forgave the payment due, especially if the appeal was regarding the first audiotex bill.
The second policy controversy was regarding "call management services." Calling number delivery (commonly known as Caller ID), the most controversial of these services, challenges the conflation of household and consumer. Contrary to telephone company puffery, the service does not truly identify a caller, but merely transmits the telephone number assigned to the location from which the call is being made. Should the called party wish to actually identify the caller by name, she must utilize some form o f directory and make additional inferences. The assumption that the "will" of the household is identical to those of its members was challenged most poignantly by women's groups who intervened in "call management service" proceedings (e.g., Manitoba Assoc iation of Women's Shelters, Inc., 1991; Grieger, 1991; see also Samarajiva & Shields, 1992). Instances of the abusive spouse disconnecting the telephone instrument from the wall jack and taking it when leaving the house (removing the abused spouse's a bility to make and receive calls) were reported and the potential uses of the calling number display device and the call return service to monitor calls to the abused spouse were pointed out. Policy analysis premised on the conflation of household and con sumer was incapable of addressing situations of coercive and abusive relations within the household (Samarajiva, 1991a). Shared access to wireless public networks through cellular and PCN devices has many similarities with household access to the wireline public network. Current pricing policies that charge for incoming calls as well as outgoing calls further complicate the sharing of access to the wireless public network.
Even though pay telephones are considered by many to be part of the wireline public network, this taxonomy locates pay telephones in a different category. A pay telephone provides direct connection to the wireline public network like a telephone set in a household. However, its user's options with regard to interexchange carriers (and perhaps other features in the future) are affected by the owner of the physical location of the pay telephone facility or some entity drawing its authority from the owner . The recent decisions of certain pay telephone operators and city governments to remove incoming call reception and touchtone capabilities in the name of the "drug war" illustrate the point.
The fourth mode of connecting to the network is through private networks interconnected to the public networks. Consumers can connect to private networks in four capacities--as residents, as voluntary "inmates" of institutions, as involuntary inmates o f institutions, and as employees qua consumers.
In the same way that administrators of these types of housing impose rules of behavior in physical space (e.g., no pets, no loud noise after a certain hour), rules of network access (or behavior in electronic space, discussed below) can be formally wri tten into contracts or incorporated into the technical design of the private network (P´ladeau, 1991) and enforced. The consumer has the choice of accepting the housing contract in toto, or finding other accommodation. The consumer's ability to make this choice or to negotiate the terms of access to the network (though this is extremely difficult if they have been embodied in the technical design) is dependent on factors other than telecommunication, namely the competitiveness of that particu lar housing market and the consumer's relative valuations of various elements of the housing package. Even this option may not be available to the consumer if the housing is a precondition of something else, such as enrollment in a university or employmen t in a factory. Here the exit option affects the consumer's education or employment, not merely his or her housing. Consumer options can be further constricted in situations where the rules of the private network are changed, by amendment of the lease or by changes in technical design, after the consumer has taken up residence. Here, the costs of moving or of breaking the lease further constrain the exit option. Family units or accommodation-sharing arrangements give rise to an additional layer of constra int/enablement.
In actual fact, the line between employee qua employee and employee qua consumer is not clear. To take the example of the call to the childcare center, what is the status of the call if the childcare center is a facility provided by the organiza tion? What if the employee is working overtime (uncompensated), and calls the baby-sitter using the organization's equipment? What if the employee is on the road on the organization's business and routes a call home via the organization's network? Does it make a difference if that call was made during working hours, or when the employee was stranded in an airport due to bad weather? Many of these questions have been resolved, leaving little if any leeway for the employee, in blue-collar work settings. But the practices of white-collar work places have traditionally been more favorable to employees. Current perturbations in this area appear to be the result of efforts to increase productivity in white-collar work places using information and communication technologies.
Some aspects of these delineation problems are likely to appear under the categories of consumers connecting to public networks (wireline and wireless) when their equipment and/or service charges are picked up by the organization because they work at h ome or on the road for the organization. This "spillover" is likely to increase with the blurring of the lines between work and leisure and between work place and home, driven in part by teleworking and personal communication technologies.
The theoretical framework used in this chapter is a communication-laden reworking of Giddens' structuration theory (1981, 1984, 1985), with emphasis on time-space and the role of recursive practices in reproducing structure. Drawing from the burgeoning multi-disciplinary inquiry (e.g., Benedikt 1992) centering on the concept of "cyberspace" (Gibson, 1984, 1987, 1988), this section seeks to rejuvenate Giddens' rather listless notion of locale. The proposed theoretical framework centers on the notion of "electronic space," reserving the Gibsonian sense of cyberspace--involving direct mind-network-mind communication--for applications more exciting than talking on the phone. Perhaps the most important idea taken from the cyberspace literature is the concep tualization of the network as a space, rather than as a conduit, or as a system of conduits. The framework introduces a cluster of related socio-spatial concepts--"space," "environment," "public space," "private space," and "electronic space". It is prese nted in greater detail in Samarajiva & Shields (1993).
Space can be understood as a terrain of human interaction. Space is produced, reproduced, and transformed by the same structural forces, social relations, and conflicts which affect social life more generally (Lefebvre, 1974/1991). Space thus produced serves as a context or resource for action: "social space is what permits fresh action to occur, while suggesting others and prohibiting yet others" (Lefebvre, 1974/1991, p. 73; also Giddens, 1979, pp. 202-206). In other words, as a social product, space is a material force which reflects back upon social processes. This is the essence of what Soja (1980; 1989, pp. 76-93) calls the "socio-spatial dialectic." Physical space can be distinguished from what Giddens describes as the "created environment" (e.g. , pastures, national parks, offices, street corners, shopping malls) defined as "a manufactured series of settings, in which even the countryside is largely ordered in terms of social influences, rather than being a 'given' world of nature" (Giddens 1989, p. 280). Humans draw upon and/or are constrained by aspects of the physical environment in the production of space. These abstract qualities of physical space and physical environment also hold true for electronic space and electronic environment.
The simplest form of physical space is constituted by the co-presence of human actors knowledgeable of each other's existence and relating in some way to each other. Aspects of an environment (e.g., the existence of walls, high noise levels) play an im portant role in the constitution of a physical space. Potential for communication (e.g., Is vision obstructed? Does sound carry? Do actors perceive the environment as conducive for interaction?) is crucial. The design of physical environments provides a p owerful vehicle for the exercise of power over actors. In his analysis of shopping malls, the modern exemplar of designed environment, Gottdiener argues that the function of mall design is "the control of crowds to facilitate consumption...to disguise the exchange relation between producer and consumer...and to present cognitively an integrated facade which facilitates this instrumental purpose by the stimulation of consumer fantasies" (1986, p. 293). Gottdiener's "socio-semiotic analysis" of control thro ugh architecture is important but overdrawn. The mall environment constrains and enables the behavior of the users in a broad sense (e.g., they cannot get out of the building without passing a lot of shops), but it does not fully "determine" specific beha viors (e.g., not every mall user forced to circumambulate shopping displays will make purchases). The mall environment only increases the probability of some of the users making shopping decisions they would not have otherwise made.
The specific relations (or lack thereof) between human actors in the environment determine the nature of the physical spaces that can be created within it. These relations are shaped, in turn, by factors such as the comparative location of the interact ants in social structure, the perceptions interactants have of these locations, the interactants' perceptions of their previous history with each other as well as their expectations concerning future relations. Depending on the nature of relations between co-present actors in a given environment, multiple physical spaces can be created in one physical environment. The existence of other spaces in the environment affects the constitution of a physical space as well, in the sense that one space is part of t he environment of another. A prisoner who occupies a physical space with his guard is constrained in the ability to create a new space with a third party, for example.
Another form of physical space is produced when one or more actors are unaware of others who are physically proximate and very much aware of them. Environment properties are particularly crucial to the formation of this space. The space constituted by a voyeur utilizing the communicational properties of a one-way mirror is an example. A more complex spatial form is constituted when subjects behave as though others are potentially co-present. The production of this space is central to the disciplinary p ower discussed by Foucault (1977). Foucault uses the panopticon, an architectural device advocated by Jeremy Bentham in 1791, to exemplify the process which gives birth to the self-policing subject. The panoptic environment consists of a watch-tower surro unded by cells enabling a guard to supervise a multitude of individually segregated prisoners. The guard cannot be observed by the prisoners. Since no prisoner can be certain of when she is not being observed, she must assume constant surveillance. Panopt icism forces individuals to self-police by exposing them to the examining gaze: "He who is subjected to a field of visibility, and who knows it, assumes responsibility for the constraints of power; he inscribes the power relation in which he simultaneousl y plays both roles" (1977, pp. 202-3). In the terms of the proposed framework, the subject is "locked" in a coercive space with a power-wielder, that is, the subject watches her own behavior so she can do what she thinks the power-wielder wants her to do. Liberation from this space comes only when the absence of surveillance is established. Foucault does not allow for this. In his vision, subjects are never "alone."
Until the advent of electronic media, all significant social interactions occurred in physical space. At the present time, we are beginning to see the emergence of electronic space. In electronic space, actors achieve conditions approaching co-presence via electronic communication media. However, electronic space can never completely supplant physical space. Certain social relations such as procreation can occur only in physical space (though proponents of cyberspace will argue otherwise (Benedikt, 199 2; Gibson, 1984, 1988)). Electronic spaces must be constituted from electronic environments and physical environments. In general, the possibilities of constraining and enabling space constitutive activities are greater in electronic environments than in physical environments. Characteristics of producing and reproducing physical and electronic environments span a wide range. In some cases, the up-front costs of producing the environment (i.e., building the plaza, establishing the network) are relatively high and the costs of reproducing it (or more conventionally, of maintaining it) are negligible. In such situations, there is a tendency to treat access to the environment as a public good (i.e., not charge for it, or bundle the costs with a related priva te good). In other cases, where the costs of reproducing the environment are relatively high, the tendency is to treat access to the environment as a private good (charge on the basis of usage). The latter type of pricing tends to reinforce the ability to control space constituting activities within the environment. The ability to regulate access to features of the environment through price as well as "technical" design features allows for a more dynamic and continuous exercise of control than is possible only with design. Electronic environments also tend to allow for easier surveillance, in the form of network management software that tracks usage patterns and purposeful information gathering and dissemination features such as calling number delivery.
A distinction may be made between public and private space, within physical and electronic space. Erving Goffman, a preeminent theorist of face-to-face interactions, defined public spaces as "any regions of a community freely accessible to members of t hat community" (1963, p. 9). A precise definition of public space must begin from physical public environments. Physical public environments are those not marked out as private by permanent or temporary markers. Highways, sidewalks, plazas, public parks, etc. would clearly fall within this category. Public as well as private spaces can be created from public environments. The range of possible spaces extend from the strongly private (e.g., lovers on a park bench) to the strongly public (e.g., police offic er directing traffic), with most of the possible spaces occupying various points in the middle of the continuum (e.g., eye-contact and body signals between two subjects communicating the yielding of a right of way in pedestrian traffic).
In essence, public spaces are characterized by a relative openness to the initiation of communication by others, and private spaces are characterized by a relative closedness to the initiation of communication by others. Openness or closedness must not be seen in terms of two well defined and mutually exclusive conditions, but as the extremes of a continuum. The negotiation of the terms and conditions of communication is an intrinsic and continuing element of every communicative relationship (Petronio, 1991).
The definitions of electronic private and public spaces are similar to those of physical private and public spaces, except for the fact that they are constituted from electronic and physical environments. The PSTN and the various e-mail capable compute r networks of today constitute electronic public spaces. These networks offer the possibility of initiating dyadic or group communication links with millions of individuals, and of having one or more of these millions of individuals initiate communication with oneself. In terms of potential, the moment of "entering" electronic space by lifting the handset or logging on to a computer network is similar to entering a physical public space where one could initiate contact with any one of the multitude inhabi ting that space, or having any one of those individuals initiate contact (but paradoxically, he is generally unreachable through the PSTN at the moment of dialing). In the case of electronic space, the possibility is that of initiating contact with a pers on or persons in that space at that moment (e.g., in the case of chatlines, or the "talk" mode in e-mail) or later when the person or persons logon (e.g., with conventional e-mail), or of initiating contact with those in physical private and public enviro nments abutting the electronic space (i.e., a telephone subscriber at home or in a pub with a telephone, a physical public space). Generally, people do not establish contact with totally unknown persons in electronic space nor in physical space. Such cont acts are initiated infrequently in electronic as well as in physical space, but the predominant pattern is for individuals to navigate their way through public space to establish contact with a known person or persons, at which point the dyad or larger gr oup effects a complete or partial withdrawal from the public space into a private space. In both physical and electronic public spaces, the possibility of unintentional collision exists, bumping into a bystander in the former and dialing a wrong number in the latter. In both physical and electronic public spaces, the boundaries of these private spaces are defined by negotiation between the communicating parties. In both physical and electronic public spaces, the boundaries between public and private space s are defined by implicit, and sometimes explicit, negotiation between the communicating parties, but also between them and third parties (Samarajiva & Shields, 1993). Infringements of these boundaries and/or the use of coercion in the negotiating pro cess constitute violations of a basic ground rule identified by Goffman (1971):
"...in Western society, as probably in all others, there is the 'right and duty of partial display.' Two or more individuals present together have the right and duty to make some information generally available concerning their relationship and the ri ght and duty to leave unsignaled other information about their relationship."(p. 198).
the capability to implicitly or explicitly negotiate boundary conditions of social relations. This definition includes control of outflow of information that may be of strategic or aesthetic value to the person and control of inflow of information, including initiation of contact. One thoughtful observer pithily described concerns over outflows as the "none-of-your-business" aspect of privacy, and concerns over inflow of information as the "leave-me-alone" aspect of privacy (Rhodes, 1991).
The proposition that the PSTN (and e-mail networks) are electronic public spaces is challenged most by the apparent lack of co-presence between the inhabitants of the electronic public space. Many would find it difficult to accept the claim that the mi llions of potential called parties are co-present on the network at any given moment. They may be out boating, at lunch, or dead, for that matter. Anyone who has used the PSTN to talk to people will point to the frequency of "telephone tag" to refute the claim of co-presence. However, as discussed above, space is also constituted when one party believes the other is potentially co-present. Discovery that the other is not there terminates the (private) space. In a public space, the expectation is not that communication with a particular person is absolutely certain, but that the potential for communication with one of many individuals exists. The absence of a particular individual does not negate the entire public space. Indeed, the unanswered telephone/an swering machine may not signify the called party's absence, but only the decision of that party to not communicate at that particular time.
If it is conceded that relationships can be established and/or sustained over electronic media, it would be necessary to accept electronic space, since space has been defined in terms of the underlying relationship. If relationships exist over asynchro nous electronic media, then we must still concede the existence of the corresponding electronic spaces. All that has to be done is to take into account the accentuated time-spanning capabilities of electronic space. If electronic space is accepted it is p ossible to treat humans as existing in physical and electronic space and to conduct research about interactions in both kinds of spaces, about how power in one kind of space is leveraged into the other, about how control over environment is translated int o power in the resultant space, and how recursive practices of agents in these spaces produce and reproduce structural power.
It is also possible to utilize the framework for policy formulation. The conceptualization of telecommunication network platforms as environments and social relations utilizing those platforms as spaces can allow telecommunication issues to be reconcep tualized as equivalent to physical space issues, enabling the adaptation and adoption of value-based policy solutions developed for those familiar spaces. While this type of analogic reasoning is tempting (particularly for those suspicious of the never-en ding, and possibly self-serving, chorus of "more research" from academics), it can be easily abused. For example, in the debate over the costs and benefits of calling number delivery services, many policy advocates rushed to draw an analogy between the ph ysical space situation of a stranger knocking at the door, and the electronic space situation of a telephone caller initiating a call. It was argued that refusing to allow number delivery was akin to wearing a paper bag over one's head when knocking at so meone's door. Others pointed to the misleading nature of this analogy, emphasizing the negotiation of identification information release in physical space and the inability of the parties to mechanically record the interaction and store and process the tr ansaction-generated information. In electronic space, both these conditions did not hold (Samarajiva, 1992).
4.0 Consumer Protection
This section assumes that direct access to the public network by the consumer is unproblematic from a policy perspective. This is far from true. First, the consumer protection regime that now exists in public networks is quite undeveloped. Second, the moves and countermoves of providers of public networks in response to private network operators, customer-premises equipment (CPE) vendors, and users, will destabilize the existing imperfect consumer protection regime. However, for the purpose of simplify ing the analysis, consumer protection afforded to sole-occupant households directly connected to the public network is held constant and used as a yardstick against which the various other modes of consumer access can be measured. A complete analysis will have to relax this assumption and analyze the system as a dynamic whole.
4.1 The Household
The household (or the family) is likely to continue to be a significant factor affecting consumer access to the public network for some time, despite industry initiatives in the areas of personal telecommunication numbers and devices tending to reduce the importance of collective and stationary access points to the network. The dependence of minor children on their parents and the persistence of collective living arrangements due to psychological and economic benefits are likely to counter-balance tend encies toward non-shared network access. Inasmuch as most family homes in North America now contain telecommunication equipment unimaginable just a decade or two ago, it is reasonable to assume that more CPE will be hooked up to the network from the house hold and that the household will increasingly resemble a private network. The abstract similarity posited by this chapter between private networks and households will become a concrete similarity.
The implications of the household as a physical space intermediating consumer access to the network may be illustrated in relation to a problem that has already reached the policy arena, that of parental control over children's access to services provi ded over the network. As network access becomes more important to children, especially teenagers, parents will seek ways to control that access. The network can be configured to assist parents (default blocking of the majority of network services) or to a ssist teenagers (non-availability of blocking, or blocking on request, or for fees). Incentives of network providers may lead them in either direction: the former because parents are present subscribers and capable of exerting political pressure; the latt er because teenagers will spend money and are future subscribers. Parents are likely to demand public policy intervention in various forms, as they have already done regarding audiotex and chatline access.
The problem may be conceptualized in terms of electronic and physical space. The household is a physical space pervaded by power. The power of the parent is never absolute, but for present purposes a power relationship skewed in favor of the parent may be assumed. The teenager's location in the physical space of the household constrains and enables her abilities to constitute other physical spaces, e.g., hanging out at the mall with friends. By methods including control of egress and ingress from the p hysical environment of the household (e.g., locking the door at a certain time), the parent can control the teenager's constitution of external spaces. In other words, the parent leverages control over the physical environment of the household (among othe r things) to control the teenager's space constitutive activities outside the parent-dominated physical space. Changes in network technologies (electronic environment) that enable the child to constitute electronic spaces outside the household tend to be dealt with in the same way. Parental efforts to have the network designed in ways that enable the leveraging of power over family and household environment to control teenagers' outside activities are similar to ensuring parental control over access to th e door keys.
The electronic space framework allows for the examination of privacy questions between members of households. As the household's electronic network approaches the sophistication of today's private networks, its surveillance capabilities will also appro ach those of such networks. Do parents have the right to collect and analyze their children's calling patterns, in the way that many business organizations analyze their employee's calling patterns using software built into their PBXs? Do the protections against unauthorized wiretaps set out in the amended Omnibus Crime Control and Safe Streets Act of 1968 (18 USCA, Title III) apply to members of households, including minors? The privacy question is integrally connected to parental or other control of acc ess to the public network. In almost all instances (except where certain forms of communication are precluded by network design), effective control of access and the enforcement of other rules requires infringement of privacy.
Once the problem is conceptualized in this manner, it is possible to either systematically investigate the implications of changing network access for the household, and thereby formulate policy, or directly frame policy based on values. Is the home a "castle" wherein the powers of the "lord"/parent are absolute, and unchallenged by government? This question has different answers in different cultures at different times. Whatever the answer is for physical space, policy could apply it to electronic spa ce (taking due care with the analogy). But this application is not simple. For those who think it is, a simple mental exercise is in order. Substitute the terms "abusive husband" for parent, and "abused wife" for child in the above discussion. How can pol icy, including policy on network design, accommodate values that privilege the needs of parents to control their children as well as values that privilege the needs of abused women?
4.2 Pay Phones
The basic issue of leveraging control over physical environment and space to control over electronic environment and space runs through many of the private-public interface issues raised by Noam (1991) and the conceptually similar, but more mundane, is sues such as problems pertaining to pay phone interfaces with the public wireline network. In the case of many pay phones, the store owner or the airport operator controls the physical location of the facility. The value of this physical location as a pay phone interface depends on adjacency to a physical public space and the amount of pedestrian or vehicular traffic within it. A part of the property rights pertaining to such a physical location is contractually assigned to the pay phone operator in retur n for payment. The pay phone operator utilizes this exclusive right to build an interface to the public network from that particular location with whatever design features she thinks will maximize returns. In other words, the pay phone operator leverages power over physical environment to create power over electronic environment. The consumer has an exit option, but in many cases there may be no other way to access the public network from the proximity of that particular physical location. Within the elec tronic environment provided by the pay phone operator, the consumer also can dial extra digits or whatever, and try to circumvent the technologically embedded rules imposed by the operator.
Generally, present-day pay telephones do not pose significant privacy problems since they do not identify the users and keep records of usage by specific persons. Of course, all pay phones pose privacy problems of a more mundane nature, in that convers ations can be overheard by bystanders. Indeed, one of the most significant privacy cases in the US, Katz v. United States (389 U.S. 347, 1967), involved the recording of a conversation in a phone booth by the Federal Bureau of Investigations. But the law in this area is settled. What is not settled is the status of information collected by credit-card and other magnetic card equipped pay phones that are becoming more common. Public policy concerns would be triggered if such features of the electronic envi ronment provided by the pay-phone operator were to be used to collect information generated by users, and to process and utilize for purposes other than completing the calls.
Again, conceptualization based on the electronic space framework can lead to policy based on research or to purely value-based policy formulation. Research can examine consumer behavior at pay phones, the relative valuation of pay phone locations, etc. In the case of value-based policy formulation, the framework directs attention to how ingress and egress paths that bear bottleneck characteristics have been dealt with in physical space. There is really not much of a difference between the basic issue a ddressed in 1877 in Munn v. Illinois (94 US 113) and the problem of delimiting the latitude pay phone operators have to constrain/enable consumer behavior. The fact that most, if not, all pay phones are located in public environments in the sense u sed by Goffman (i.e., public not because of government or other forms of public property rights, but by reason of more or less open access), distinguishes the pay phone problem both from the above discussed problem of household access and the problems of access to the public network via private networks, discussed below. It must, however, be emphasized that the location of pay phones in public environments does not imply a claim that the electronic spaces constituted by their users are public as well. As discussed in Section 3.0, private physical or electronic space can be constituted from public environments.
4.3 Private Networks
Of the four sub-categories of connections to the PSTN through private networks outlined above, the resident and voluntary "inmate" categories can be dealt with together since the essential difference between them is duration of stay. Here, the basic pr oblem is that physical environment (e.g., dormitory, hotel room) is being bundled with a particular form of electronic environment. Control over physical environments is being extended to electronic environments through the process of bundling. Generally speaking, antitrust law frowns upon the extension of market power from one market to another through bundling. But whether this is being done or not in cases falling under these categories is an empirical question. It is possible that there is really no m arket power in the hotel industry in a particular region, even if one hotel bundles network access with the hotel room in a particularly undesirable form. One problem in undertaking this type of analysis at the present time is that network access constitu tes such a minuscule portion of the bundled package. But with the increasing importance of network access, it may become more commensurate with the other elements of the bundle of services offered by a hotel or similar institution.
Another way of coming at the problem is to identify situations where the exit option is severely limited, e.g., where accepting dormitory accommodation is a pre-condition of studying at a particular university. Public policy could identify a threshold of involuntariness beyond which certain safeguards for consumers would kick in. Hospitals where patients cannot make exit decisions due to medical or insurance factors, university dormitories where residence is compulsory, company towns where residence is a condition of employment, etc. would thus be subject to a different standard than the single hotel in an airport strip that prevents a consumer from calling a 900 number. The publicness of the institution, either in terms of ownership or in terms of pub licness of purpose, may also be factored into the policy equation.
Access to the public network via private networks by involuntary inmates of institutions poses a somewhat easier problem. These consumers have always had their physical-space egress and ingress controlled. Extending that control to electronic space doe s not mark a radical change. The only problematic areas are where the levels of control in the two forms of space differ dramatically, or where the manner of control is inconsistent with contemporary standards for the treatment of incarcerated persons. Th e formulation of the problem as one involving two different forms of social space enables research to be conducted, or policy to be formulated based on value judgments. If the applicable values hold that solitary confinement for long periods of time is cr uel and unusual punishment, it would not be unreasonable to infer that complete prohibition of access to the public network also constitutes cruel and unusual punishment. In the same way that prisoners are allowed different forms of interactions in physic al space, ranging from conjugal visits to guard-observed, no-physical contact conversations, prisoners may be allowed different forms of electronic-space interactions as well. p>Conceptualizing incarceration as the coercive restriction of a person's ability to constitute physical and electronic spaces leads to an interesting idea for releasing pressure on prison space. Why not punish certain kinds of crimes by restricting the a bility to constitute electronic spaces only? The Secret Service and other law enforcement agents pursuing "hackers" and "crackers" appear to have hit upon this idea before anybody else, evidenced by their proclivity to "confiscate" all network interface e quipment in the suspects' households. There is an apocryphal story about Kevin Mitnik (one of earliest "phreakers" to be apprehended) being served with an injunction not to go within five feet of a telephone. I have suggested on an earlier occasion (Samar ajiva, 1991b) that obscene and harassing callers should be punished by having network privileges withdrawn or curtailed. I recognize that problems of enforcement and civil liberties must be carefully examined. Yet, the idea of meting out electronic punish ment for electronic crimes, which could also affect recidivism, appears to be worth serious consideration.
The employee sub-category is quite complex. In legalistic terms, it can be argued that an employee cannot be a consumer on "company time" and using the employer's equipment. Most concerns about the attrition of employees' rights in relation to network access appear to refer to white-collar employees. Blue-collar employees have rarely enjoyed rights or privileges to engage in consumer activities on "company time" using company facilities, with the exception of certain customary rights built up in specif ic plants over the years. White-collar employees who enjoyed more flexible work conditions, and who usually do not differentiate between "company time" and personal or leisure time as clearly as blue-collar workers do, had built up a different set of righ ts and privileges with regard to telephone use, newspaper reading, and so on. The contemporary drive for increased office productivity has threatened some of these rights and privileges, including some relatively new practices such as playing computer gam es on office computers. So what is really at issue is not whether the formal legal rights of employees to free association and speech are being taken away by the new technologies. It is whether changes to customary practices within white-collar work place s (and to a degree, within blue-collar work places) being implemented partly through technical design of information communication technologies (e.g., PABXs that monitor outgoing calls by number and duration, computers that count keystrokes), and partly t hrough new work rules are justified. Again, the question ceases to be a purely telecommunication question, but instead becomes one of socially acceptable working conditions.
The problem of access to the network by employees for consumer purposes is somewhat tractable in standard work-places where distinctions between work-time and leisure-time, and between the employer's facilities and the employee's equipment are clearly demarcated. But more and more, these distinctions are becoming blurred in many employment situations. The truly difficult problems lie in these gray areas. Many employees, particularly those in creative or management positions, tend to work outside hours in work-places and/or take work home. Telework brings company computer and communication equipment into employees' homes. Employees on the move carry company communication equipment around with them on their persons or in their vehicles. The potential for dual uses of time and equipment is enormous. Preventing dual use by making demarcations between work-related space and personal space sharper is rather unrealistic at this stage. But the other solution of increasing the surveillance capabilities of the t echnologies runs counter to many contemporary social values. It appears that a different approach to the problem, perhaps one involving output-based performance criteria and disclaimer of all authority over how the work gets done and how the equipment is used, needs to be devised.
Surveillance and privacy issue are extremely important in relation all forms of private networks. The control by private network operators that concerns Noam will be actually operationalized through surveillance-related practices. Using existing techno logical features all these networks are capable of collecting detailed transaction records and of analyzing them in rather sophisticated ways (e.g., which employees called a particular number; the most-called number by employee; duration per call). In man y cases, the private network operator will claim that such monitoring is required for billing purposes (residences, hotels, hospitals, etc.) or for control purposes (prisons, offices, etc.). They may even claim that such monitoring is required to fulfill legal obligations. In some cases, these rationales lead to the routine comprehensive or random taping of telephone conversations as such. Operators will exercise control over their networks by direct surveillance or by inducing self-policing through panop tical means. The latter could yield a form of control that is more pervasive, extensive, and economical than would be the case with direct surveillance (for discussion, see Samarajiva & Shields 1992; Gandy 1993). Space limitations preclude a detailed discussion of these important issues here, particularly because much of the practice and law on this area is unsettled and problematic.
5.0 Concluding Comments
This chapter has developed a taxonomy of forms of access to the decentralized network, proposed a theoretical framework for analyzing the consumer protection implications, and examined the principal consumer protection issues in each of the forms of ac cess. The taxonomy enables the extension of the scope of Noam's concerns regarding power of private network operators to a range of forms of access, unproblematic on the surface, but tending toward convergence with private networks in the near future.
The application of the theoretical framework of electronic space to problems of consumer protection pertaining to access to the public network opens up a number of possibilities for framing research questions and for formulating public policy. While no t yielding empirically testable hypotheses, the theoretical framework prepares the ground for empirical investigation. It focuses the researcher on the proper questions and relationships to investigate. It can guide research on the range of forms of acces s identified in the taxonomy, from the household to "private" use of corporate networks by employees. The research agenda derived from this framework would include ethnomethodological investigations of household and workplace behavior regarding telecommun ication usage (including the identification of rules governing such usage) and analyses of market power in relation to pay phones, hotels, hospitals and other types of private network operators.
The framework can also be utilized to guide policy formulation on the basis of values in conjunction with, and in even in lieu of, research findings. What is particularly interesting is how the application of the framework to consumer protection issues that are ostensibly within the province of telecommunication policy transforms them into family policy, competition policy, labor policy and such general policy issues. This should not come as a surprise because telecommunication networks are utilized in the production and reproduction of social relations and are not a distinct and self-contained sphere of activity.
Bibliography
Benedikt, M. (Ed.). (1992). Cyberspace: First steps. Cambridge, MA: MIT Press.
Carterfone device in message toll telephone service, [In the matter of the use of the]. 13 FCC 2d 420 (1968), recon. denied, 14 FCC 2d 571 (1968).
Foucault, M. (1977). Discipline and punish: The birth of the prison. (A. Sheridan, Trans.). New York: Vintage.
Gandy, O.H., Jr. (1993). The panoptic sort: A political economy of personal information. Boulder CO: Westview.
Gibson, W. (1984). Neuromancer. New York: Ace Books.
Gibson, W. (1987). Count Zero. New York: Ace Books.
Gibson, W. (1988). Mona Lisa Overdrive. New York: Bantam Books.
Giddens, A. (1979). Central problems in social theory. Berkeley: University of California Press.
Giddens, A. (1981). A contemporary critique of historical materialism, vol 1. London: Macmillan.
Giddens, A. (1984). The constitution of society. Cambridge: Polity Press.
Giddens, A. (1985). The nation-state and violence: A contemporary critique of historical materialism, vol 2. Cambridge: Polity Press.
Giddens, A. (1989). A reply to my critics. In D. Held & J.B. Thompson (Eds.), Social theory of modern societies: Anthony Giddens and his critics (pp. 249-301). Cambridge: Cambridge University Press.
Goffman, E. (1963). Behavior in public places: Notes on the social organization of gatherings. New York: The Free Press.
Gottdiener, M. (1986). Recapturing the center: A semiotic analysis of shopping malls. In M. Gottdiener & A.P. Lagopoulos (Eds.), The city and the sign: An introduction to urban semiotics, (pp. 288-302). New York: Columbia University Press.
Grieger, W. (1991). Testimony on behalf of the Manitoba Association of Women's Shelters, Inc., before the Public Utilities Board of Manitoba at the Public Hearing on the Application by the Manitoba Telephone System for an Order Approving a Trial of Cal l Management Services, 10 December.
Hirschman, A. (1970). Exit, voice and loyalty: Responses to decline in firms, organizations, and states. Cambridge MA: Harvard University Press.
Katz v. United States (389 U.S. 347, 1967).
Lefebvre, H. (1991). The production of space (D. Nicholson-Smith, Trans.). Oxford: Basil Blackwell (Original work published 1974).
Manitoba Association of Women's Shelters, Inc. (1991). Documentation of concern submitted to Manitoba Public Utilities Board on April 25.
Munn v. Illinois. 94 U.S. 113 (1877).
Noam, E. (1991). Private networks and public objectives. In Universal telephone service: Ready for the 21st century? Annual review of the Institute for Information Studies (pp. 1-27). Nashville TN & Queenstown MD: Northern Telecom & Aspe n Institute.
Omnibus Crime Control and Safe Streets Act of 1968 (18 USCA, Title III).
Péladeau, P. (1991). The informational privacy challenge: The technological rule of law. In R. I. Chlewinski (ed.) Human rights in Canada: Into the 1990s and beyond. Ottawa: Human Rights Research and Education Centre.
Petronio, S. (1991). Communication boundary management: A theoretical model of managing disclosure of private information between marital couples. Communication Theory, 1(4), 311-335.
Samarajiva, R. (1991a). Answers to cross-examination, following testimony before the Public Utilities Board of Manitoba at the Public Hearing on the Application by the Manitoba Telephone System for an Order Approving a Trial of Call Management Services , 19 December.
Samarajiva, R. (1991b). Telecommunication privacy: Caller ID and customer information, presentation at the Washington Utilities and Transportation Commission, Olympia WA, June 12.
Samarajiva, R. (1992). The "intelligent network": Implications for expression, privacy, and competition. In W.H. Melody (ed.) The intelligent telecommunication network: Privacy and policy implications of calling line identification and emerging info rmation services: Proceedings of a CIRCIT conference (pp. 34-60). Melbourne: CIRCIT.
Samarajiva, R. & Mukherjee, R. (1991). Regulation of 976 services and dial-a-porn: Implications for the intelligent network. Telecommunications Policy, 15(2): 151-64.
Samarajiva, R. & Shields, P. (1992). Emergent institutions of the "intelligent network": Toward a theoretical understanding. Media, Culture and Society, 14(3), 397-419.
Samarajiva, R. & Shields, P. (1993). Institutional and strategic analysis in electronic space: A preliminary mapping, paper presented at the 43rd annual conference of the International Communication Association, May 27-31, Washington DC.
Soja, E.W. (1980). The socio-spatial dialectic. Annals of the Association of American Geographers, 70, 175-190.
Soja, E.W. (1989). Postmodern geographies: The reassertion of space in critical social theory. London: Verso.
Note 1: This broad meaning is included in all references to "calls" and "calling" and "being called" in this paper. Back.
Note 2: Extracted from Samarajiva & Shields (1993). Back.